Navigating a technical interview for a networking role can be daunting. Success hinges not just on knowing the answers, but on demonstrating a deep, practical understanding of core concepts. This guide breaks down the 10 most critical networking interview questions you're likely to face, moving beyond simple definitions to provide expert-level answers, common pitfalls to avoid, and strategic tips to make you stand out.
Whether you're aiming for a role in network administration, cybersecurity, or cloud engineering, mastering these topics will equip you with the confidence and knowledge to impress any hiring manager. We'll explore everything from the foundational OSI model and the differences between TCP and UDP, to complex routing protocols and practical troubleshooting methodologies. Our goal is to ensure you're prepared to articulate not just what a technology is, but why it's used and how it functions in a real-world scenario.
This comprehensive preparation is crucial, especially for those targeting roles in Germany's competitive tech market. To truly unlock your next role, mastering the art of connecting with industry professionals is as vital as preparing for technical questions. Consider how you can leverage AI for professional networking to expand your opportunities and make meaningful connections. For personalised interview coaching, platforms like iknowly connect you with experts from top German companies, offering 1:1 sessions to perfect your technique and align your skills with local employer expectations. This guide provides the technical foundation; effective networking will help you get your foot in the door.
1. Explain the OSI Model and its 7 layers
This is one of the most fundamental networking interview questions, as the OSI (Open Systems Interconnection) model provides the conceptual bedrock for all network communications. It is a standardised, seven-layer framework that breaks down the complex process of sending data from one device to another into smaller, more manageable tasks.
Answering this question effectively demonstrates your core technical knowledge and ability to think logically about data flow and troubleshooting. Interviewers use it to gauge your understanding of how different network protocols and hardware components interact to create a functional system.
How the OSI Model Works
Each of the seven layers has a distinct responsibility and communicates only with the layers directly above and below it. Data moving down the stack is encapsulated (wrapped with header information) at each layer, and de-encapsulated as it moves up the stack on the receiving end.
- Layer 7 (Application): The layer closest to the end-user. It provides network services directly to user applications. Examples include HTTP for web browsing, SMTP for email, and FTP for file transfers.
- Layer 6 (Presentation): Translates, encrypts, and compresses data, ensuring it is in a usable format for the Application layer.
- Layer 5 (Session): Establishes, manages, and terminates connections (sessions) between applications.
- Layer 4 (Transport): Provides reliable data transfer between end systems, handling flow control and error correction. Key protocols are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
- Layer 3 (Network): Responsible for logical addressing (IP addresses) and routing packets across different networks to their final destination. Routers and protocols like OSPF and BGP operate here.
- Layer 2 (Data Link): Manages physical addressing (MAC addresses) and controls how data is placed onto and retrieved from the physical medium. Switches operate at this layer.
- Layer 1 (Physical): Defines the physical and electrical specifications for the network, including cables, connectors, and wireless signals. It transmits raw data as bits.
The infographic below illustrates how data is processed at key layers as it travels from a user application down to the physical network.
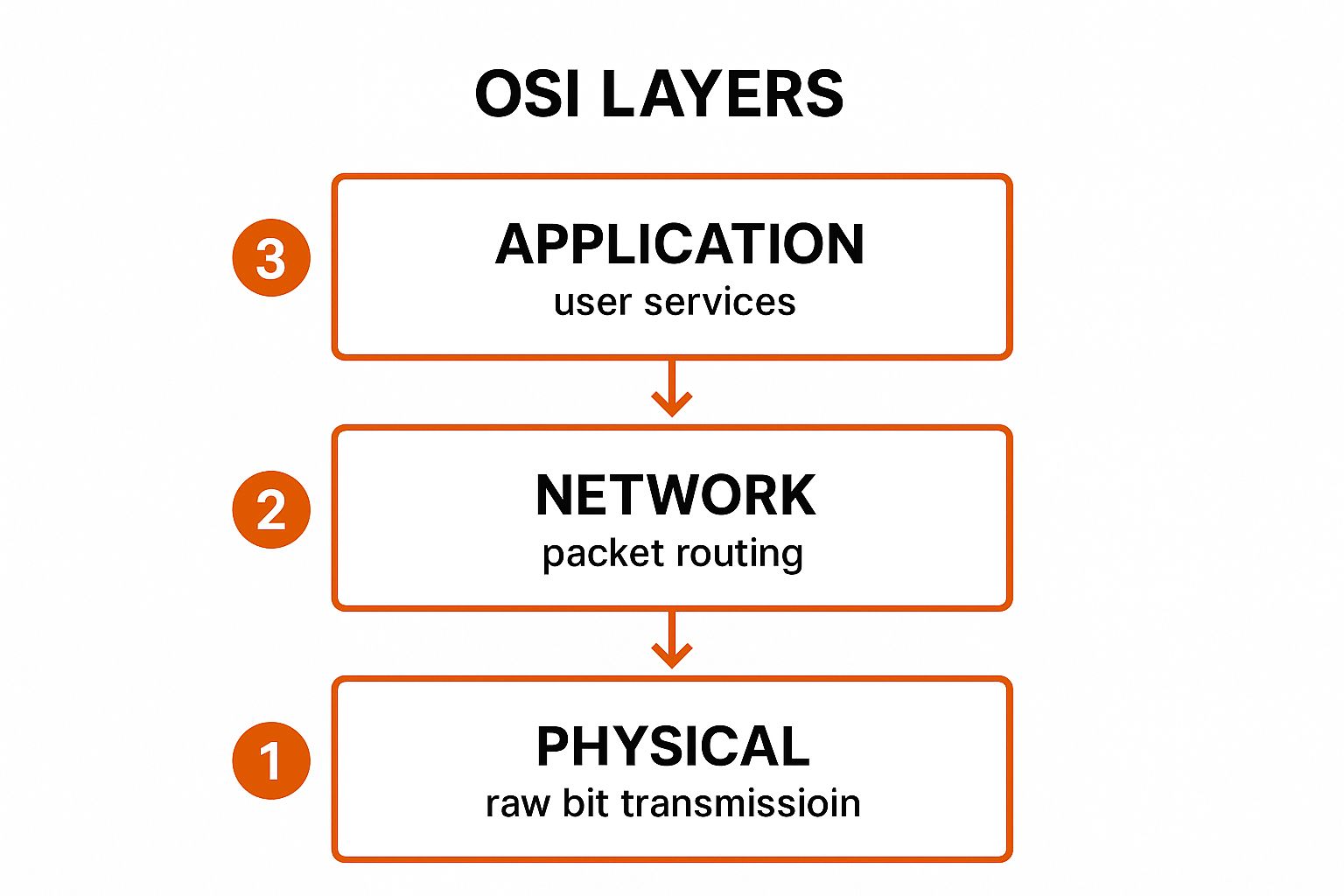
This visual flow highlights the model's core function: abstracting complex processes into distinct, sequential stages, from user-facing services down to physical bit transmission.
How to Prepare Your Answer
When preparing for an interview, especially in a competitive market like Germany, it is crucial to go beyond simple memorisation. While mnemonics like "Please Do Not Throw Sausage Pizza Away" are useful, a strong candidate connects theory to practice. For instance, explain how you would use your knowledge of the OSI model to troubleshoot a connectivity issue, starting at the Physical layer and working your way up. Understanding this framework is as foundational as preparing for common conversational questions; you can get insights into preparing for those by reviewing resources that cover a wide range of German interview questions and answers.
2. What is the difference between TCP and UDP?
This question is a cornerstone of networking interviews, designed to test your understanding of how data is actually moved between systems. TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are the two primary protocols at the Transport Layer (Layer 4) of the OSI model. Your ability to articulate their differences, including their respective strengths and weaknesses, reveals your depth of knowledge about data integrity, speed, and application requirements.
Interviewers use this question to evaluate if you can apply theoretical concepts to practical scenarios. Differentiating between these protocols is crucial for network design, performance optimisation, and troubleshooting, showing you can make informed decisions about which protocol is suitable for a specific application.
How TCP and UDP Work
The fundamental difference lies in their approach to data transmission. TCP is connection-oriented, whereas UDP is connectionless.
- TCP (Transmission Control Protocol): Establishes a reliable, ordered, and error-checked connection before sending any data. It uses a three-way handshake (SYN, SYN-ACK, ACK) to create a session. If a data packet is lost, TCP ensures it is re-sent. This reliability, however, comes at the cost of higher overhead and slower speeds.
- Use Cases: Web browsing (HTTP/HTTPS), email (SMTP/IMAP), and file transfers (FTP), where data integrity is paramount.
- UDP (User Datagram Protocol): A much simpler, connectionless protocol. It sends data packets (datagrams) without establishing a prior connection or guaranteeing delivery, order, or error checking. Its low overhead makes it significantly faster than TCP.
- Use Cases: Real-time applications like video streaming, online gaming, Voice over IP (VoIP), and DNS, where speed is more critical than 100% data reliability.
How to Prepare Your Answer
A strong answer goes beyond simply stating that TCP is "reliable" and UDP is "fast". You need to demonstrate a nuanced understanding of the trade-offs involved and connect them to real-world applications.
Be prepared to explain the TCP three-way handshake process in detail. Discuss scenarios where you would choose one protocol over the other and justify your decision based on application needs like latency sensitivity versus data integrity. Highlighting these practical considerations is a key skill, much like the strategic thinking required for technical project oversight. You can explore this further by reviewing typical program manager interview questions, which often test similar decision-making abilities. Mentioning key concepts like flow control in TCP also shows a deeper level of expertise.
3. How does DHCP work and what are its components?
This question probes your knowledge of network automation and IP address management, which are core tasks for any network professional. DHCP (Dynamic Host Configuration Protocol) is the protocol that automates the assignment of IP addresses, subnet masks, default gateways, and DNS server addresses to devices on a network.
Interviewers ask this to verify your understanding of how a network scales and how client devices get online without manual configuration. Explaining it well shows you grasp essential, practical networking concepts beyond just theoretical models.
How DHCP Works
DHCP operates on a client-server model and is famous for its four-step process, often remembered by the mnemonic DORA. This process allows a client to lease an IP address from a server for a specific duration.
- Discover: A client device new to the network broadcasts a DHCPDISCOVER message to find any available DHCP servers on the local network segment.
- Offer: DHCP servers that receive the discover message respond by sending a DHCPOFFER message back to the client. This message contains a proposed IP address and other network configuration parameters.
- Request: The client receives one or more offers and chooses one. It then broadcasts a DHCPREQUEST message, formally requesting the offered IP address from the selected server.
- Acknowledge: The chosen DHCP server finalises the process by sending a DHCPACK (Acknowledgement) message. This confirms the IP address lease and provides any remaining configuration details. The client can now use the IP address.
This automated process is fundamental to modern networks, from a small home setup where a router acts as the DHCP server to large enterprise environments managing thousands of IP addresses.
How to Prepare Your Answer
A strong answer moves from the "what" to the "how" and "why." Instead of just reciting the DORA steps, connect them to practical scenarios and troubleshooting.
Your preparation should focus on demonstrating a deeper, more practical understanding. For example, mention DHCP relay agents, which are used to forward DHCP requests across different subnets, a common scenario in enterprise networks. Also, be ready to discuss setting up DHCP reservations to assign a permanent IP address to a specific device like a printer or server. Finally, understanding DHCP options (like option 66 for TFTP server addresses) shows you have a nuanced grasp of the protocol's full capabilities.
4. Explain how DNS resolution works
This question is a cornerstone of networking interviews because DNS (Domain Name System) is the internet's phonebook. It translates human-friendly domain names (like google.com) into the numerical IP addresses that computers use to communicate. Without DNS, navigating the web would be impractical.
Interviewers ask this to test your understanding of a fundamental internet service. A clear explanation shows you grasp how critical infrastructure components interact and appreciate the concepts of distributed systems and caching, which are vital for network performance and reliability.
How DNS Resolution Works
The process is a hierarchical query sequence that typically involves several servers. When you type a domain into your browser, a request is sent to a recursive resolver (usually provided by your ISP or a public service like Cloudflare). If the resolver doesn't have the IP address cached, it begins a multi-step process:
- Recursive Resolver to Root Server: The resolver asks a root DNS server for the location of the Top-Level Domain (TLD) server. The root server responds with the address of the
.comTLD server. - Resolver to TLD Server: The resolver then queries the
.comTLD server, asking for the authoritative name server forgoogle.com. The TLD server provides this information. - Resolver to Authoritative Server: Finally, the resolver queries the authoritative name server for
google.com. This server holds the actual DNS records for the domain and returns the correct IP address (e.g., an A record for IPv4). - Caching: The recursive resolver caches this IP address for a specific period (defined by the Time-To-Live or TTL value) and sends it back to your computer. Future requests for the same domain can be answered instantly from the cache.
This sequence can be either recursive (the resolver does all the work on behalf of the client) or iterative (the client is referred to the next server in the chain and must make the query itself). Most client-to-resolver queries are recursive.
How to Prepare Your Answer
A strong answer goes beyond listing the steps. You should demonstrate practical knowledge. Mention command-line tools like nslookup (Windows) or dig (Linux/macOS) to show you can actively query DNS records and troubleshoot issues. Discuss common record types and their functions:
- A Record: Maps a domain to an IPv4 address.
- AAAA Record: Maps a domain to an IPv6 address.
- CNAME Record: Creates an alias, pointing one domain to another.
- MX Record: Specifies the mail servers responsible for a domain.
Explain the importance of caching and TTL, as they are crucial for reducing latency and network traffic. For a deeper, practical understanding, you can explore how these settings are managed on different systems. For instance, a detailed guide on cómo cambiar DNS en tus dispositivos can offer hands-on insight into how users can influence this resolution process for better performance or security. This practical application solidifies your theoretical knowledge for any networking interview questions.
5. What is subnetting and how do you calculate subnet masks?
This is a classic among networking interview questions, designed to test your practical, hands-on knowledge of IP addressing. Subnetting is the process of dividing a single, large network into multiple smaller, more manageable subnetworks, or "subnets". The ability to perform these calculations quickly and accurately is a core skill for any network professional.
Interviewers ask this to verify your understanding of network design, IP address conservation, and performance optimisation. A strong answer demonstrates that you can think logically about network architecture and apply mathematical principles to solve real-world problems, such as segmenting a corporate network for different departments.
How Subnetting Works
Subnetting works by "borrowing" bits from the host portion of an IP address and using them for the network portion. This creates additional network IDs within the original address block. The subnet mask is what tells devices which part of the IP address is the network portion and which part is the host portion.
For example, take a standard Class C network like 192.168.1.0/24. The /24 means the first 24 bits are for the network, leaving 8 bits for hosts. If you borrow 2 bits from the host portion, your new subnet mask becomes /26 (24+2). This change creates four distinct subnets, as 2 to the power of 2 (2^2) is 4. Each new subnet has fewer available host addresses but allows for better network organisation and security.
How to Prepare Your Answer
A theoretical explanation is good, but demonstrating the calculation is crucial. Be prepared to work through an example on a whiteboard or paper.
- Master Binary: Subnetting is fundamentally a binary operation. Be comfortable converting between binary and decimal notation quickly.
- Know the Formulas: Remember the key formulas: 2^n (where n is the number of borrowed bits) to calculate the number of subnets, and (2^h) – 2 (where h is the number of remaining host bits) to find the number of usable hosts per subnet.
- Practise Scenarios: Work through examples with different network classes (A, B, and C). For instance, calculate the subnets and host ranges for a 10.0.0.0/8 network that needs to be divided into 50 subnets.
- Define Key Addresses: Clearly explain the purpose of the network address (the first address in the range) and the broadcast address (the last address), and why they are not assignable to hosts.
6. Describe the difference between a switch and a router
This is another classic among networking interview questions, as it tests your understanding of the core hardware components that build a network. While both devices manage data traffic, they operate at different layers of the OSI model and serve fundamentally distinct purposes. Getting this right shows you can differentiate between local and wide-area networking concepts.
Interviewers ask this question to verify your grasp of data forwarding principles, addressing schemes, and network segmentation. A clear answer demonstrates that you understand not just what these devices are, but how they work together to facilitate communication from a local printer to a server on the other side of the world.
How Switches and Routers Work
The primary distinction lies in the OSI layer at which they operate. A switch works at Layer 2 (Data Link), while a router operates at Layer 3 (Network). This operational difference dictates how they handle data and make forwarding decisions.
- Switch (Layer 2): A switch connects devices within the same local area network (LAN), like computers and printers in an office. It uses MAC (Media Access Control) addresses to forward data frames to the correct device. Switches create a MAC address table to learn which devices are connected to which ports, ensuring data is sent only to its intended recipient within the LAN. Importantly, switches do not block broadcast traffic, meaning a single broadcast message will be sent to all connected devices.
- Router (Layer 3): A router's main job is to connect different networks together, such as connecting your home LAN to the internet (a wide area network, or WAN). It uses IP (Internet Protocol) addresses to route data packets between these networks. Routers make intelligent decisions about the best path for data to travel. A crucial function of a router is that it breaks up broadcast domains, preventing broadcast traffic from one network from flooding another.
How to Prepare Your Answer
Beyond simply stating the OSI layers, a strong candidate will provide a practical example of the data flow. Describe how a packet travels from a PC, through a switch to a local router, and then out to the internet, explaining the role each device plays in the journey. This showcases a deeper, operational understanding.
- Emphasise that switches operate within a single broadcast domain, using MAC addresses for local delivery.
- Explain that routers operate between broadcast domains, using IP addresses to find the best path to a remote network.
- Mention that many modern home devices are combination units, acting as a router, switch, and wireless access point all in one.
Understanding these foundational hardware roles is a key step in building your networking expertise. Integrating this knowledge into a structured growth plan is essential for career progression, and you can learn more about creating a comprehensive career development plan to map out your next steps.
7. What are VLANs and how do they work?
This is another cornerstone of networking interview questions, as Virtual Local Area Networks (VLANs) are fundamental to modern network design. VLANs allow administrators to segment a physical network into multiple, distinct logical networks. This means devices can be grouped together even if they are not connected to the same physical switch.
Interviewers ask this question to assess your practical knowledge of network segmentation, security, and traffic management. A strong answer demonstrates that you understand how to build efficient, secure, and scalable network infrastructures beyond basic physical connections.
How VLANs Work
VLANs work by logically dividing a single physical switch into multiple virtual switches. Each VLAN creates an isolated broadcast domain, meaning traffic from one VLAN is not forwarded to another unless explicitly routed between them. This is achieved using a process called VLAN tagging.
- VLAN Tagging (IEEE 802.1Q): When a data frame travels between switches over a special link called a trunk port, a "tag" is inserted into the frame's header. This tag contains the VLAN ID, which tells the receiving switch which VLAN the frame belongs to.
- Access Ports: These ports connect to end devices like computers or printers. They are assigned to a single VLAN and do not understand VLAN tags; the switch adds the tag when the frame leaves an access port to cross a trunk, and removes it before sending the frame to an end device.
- Trunk Ports: These ports are configured to carry traffic for multiple VLANs simultaneously between switches or to a router. They are essential for inter-VLAN communication and extending VLANs across a large network.
For example, a corporate network can use VLAN 10 for employees, VLAN 20 for guests, and VLAN 30 for servers. Even if all devices are plugged into the same physical switch, traffic from a guest's laptop in VLAN 20 will not be visible to an employee's computer in VLAN 10, significantly enhancing security.
How to Prepare Your Answer
A comprehensive answer should connect the theory of VLANs to practical application and security considerations. Merely defining a VLAN is not enough; you need to show you understand its operational nuances.
Focus on explaining the distinction between access ports (for end devices) and trunk ports (for inter-switch links). Mention the IEEE 802.1Q protocol as the standard for VLAN tagging. It is also beneficial to discuss the concept of a native VLAN on a trunk link and its security implications, such as the risk of VLAN hopping attacks if not configured correctly. Demonstrating this deeper, security-conscious knowledge will set you apart from other candidates.
8. Explain routing protocols: RIP, OSPF, and BGP
Understanding how routers share information to build their forwarding tables is crucial for any network professional. This question tests your knowledge of the core algorithms that enable network communication, moving beyond basic connectivity to the logic of path selection. Interviewers ask this to assess your grasp of routing dynamics, scalability, and protocol selection for different network scenarios.
A strong answer demonstrates that you can differentiate between routing protocol classes (distance-vector, link-state, path-vector) and articulate the specific use cases for each. It shows you can think critically about network design and its requirements, a key skill for advanced roles.
How These Routing Protocols Work
Routing protocols allow routers to dynamically learn about available networks and determine the optimal path to forward data packets. While all serve this general purpose, their mechanisms, scalability, and complexity differ significantly.
- RIP (Routing Information Protocol): A basic distance-vector protocol that uses hop count as its primary metric. Routers running RIP periodically broadcast their entire routing table to their direct neighbours. It is simple to configure but suffers from slow convergence and is limited to a maximum of 15 hops, making it unsuitable for large, modern networks.
- OSPF (Open Shortest Path First): A more sophisticated link-state protocol designed for use within a single autonomous system (an internal network). Instead of sharing entire tables, routers exchange information about their direct connections (link states). Each router then independently calculates the shortest path to all destinations using the Dijkstra algorithm, leading to faster convergence and greater scalability than RIP.
- BGP (Border Gateway Protocol): The path-vector protocol that makes the internet work. It is an exterior gateway protocol (EGP) used to exchange routing information between different autonomous systems (e.g., between internet service providers). BGP makes routing decisions based on paths, network policies, and a wide range of attributes, not just a simple metric like speed or hop count.
How to Prepare Your Answer
Beyond defining each protocol, a top-tier candidate will compare their characteristics and explain the decision-making process for choosing one over another. This is one of the more advanced networking interview questions, so demonstrating practical knowledge is key.
Focus on the "why" behind each protocol. Explain that you would use RIP only for a very small, simple office network due to its limitations. Describe how OSPF is the standard for most enterprise-level internal networks because of its efficiency and scalability. Finally, clarify that BGP is the mandatory protocol for connecting an organisation to the internet or linking large, geographically dispersed corporate sites. Mentioning concepts like administrative distance to explain how a router prioritises routes learned from different protocols will further strengthen your answer.
9. What is NAT (Network Address Translation) and why is it used?
This question is a cornerstone of modern networking interviews, as NAT (Network Address Translation) is a critical technology used in nearly every network, from home offices to large enterprises. It addresses the fundamental problem of IPv4 address exhaustion and provides a basic layer of security.
Interviewers ask this to assess your understanding of IP addressing, network security principles, and practical problem-solving. A strong answer shows you grasp how internal networks connect to the public internet securely and efficiently, a key skill for any network professional.
How NAT Works
NAT is the process of modifying IP address information in packet headers while they are in transit across a routing device. Its primary function is to map private, non-routable IP addresses (like those in the 192.168.x.x range) to a single public, routable IP address, allowing multiple devices on a private network to share one internet connection.
When a device on the private network sends a packet to the internet, the NAT-enabled router replaces the private source IP address with its own public IP address. It keeps a record of this translation in a NAT table, so when a response comes back, it knows which internal device to forward the packet to.
- Static NAT: A one-to-one mapping where a specific private IP address is always translated to the same public IP address. It is often used to make an internal server accessible from the internet.
- Dynamic NAT: Maps private IP addresses to a public IP address from a pool of available public addresses. The mapping is temporary and assigned on a first-come, first-served basis.
- Port Address Translation (PAT): Also known as NAT Overload, this is the most common type. It maps multiple private IP addresses to a single public IP address by using different source port numbers to distinguish between connections. This is how a typical home router allows all your devices to use one internet connection.
How to Prepare Your Answer
Beyond defining the concept, a prepared candidate should discuss its real-world implications. Being ready to discuss the different types of NAT and their specific use cases will set you apart.
Focus on connecting theory to practice. For example, explain how you would use PAT in a corporate environment to provide internet access to hundreds of employees using a limited number of public IPs. Also, be prepared to discuss NAT's limitations, such as how it can complicate certain protocols like FTP or VoIP, and how techniques like port forwarding or NAT traversal are used to overcome these challenges. This demonstrates a deeper, more practical understanding that German employers highly value.
10. How do you troubleshoot network connectivity issues?
This is one of the most critical, practical networking interview questions an employer can ask. It moves beyond theoretical knowledge to assess your hands-on problem-solving abilities, logical thinking, and methodical approach under pressure. How you answer reveals your real-world experience and your capacity to restore vital services efficiently.
Interviewers ask this to see if you can apply a structured methodology, rather than randomly trying solutions. A strong answer demonstrates your ability to systematically diagnose and resolve problems, a core competency for any networking professional. It shows you can be trusted to handle outages and performance degradation in a live environment.
A Systematic Troubleshooting Approach
The best approach is typically a layered one, often following the OSI or TCP/IP model from the bottom up. This ensures you verify foundational elements before moving to more complex, abstract layers. A logical workflow prevents wasted time and ensures no potential cause is overlooked.
- Step 1 (Physical Layer): Start with the basics. Is the cable plugged in? Are there link lights on the switch and network interface card (NIC)? This layer addresses physical connectivity issues like faulty cables, loose connections, or hardware failure.
- Step 2 (Data Link/Network Layer): Once physical connectivity is confirmed, check logical connectivity on the local network. Can the device get an IP address via DHCP? Use
ipconfigorifconfigto verify. Usepingto test reachability to the default gateway and other local devices. - Step 3 (Network/Transport Layer): If local connectivity is fine, test wider network and internet reachability. Use
traceroute(ortracerton Windows) to map the path to a destination and identify where packets are being dropped. Check for firewall rules or access control lists (ACLs) that might be blocking traffic. - Step 4 (Application Layer): If network-level tests succeed but a specific service fails (e.g., a website won't load), investigate the application. Use
nslookupordigto check for DNS resolution issues. Use tools liketelnetornetcatto test if the specific port is open on the destination server.
How to Prepare Your Answer
Your response should be a narrative that walks the interviewer through your thought process. Don't just list tools; explain why and when you would use each one in a logical sequence. Be prepared to discuss a specific example from your past experience where you successfully resolved a connectivity problem.
Frame your answer around a systematic, top-down or bottom-up methodology. For instance, explain that you "always start at the Physical layer to rule out simple hardware issues before moving up the stack." This structured thinking is highly valued. Understanding the common challenges and solutions is crucial, especially when building a networking career in a competitive landscape. You can learn more about the specifics of the networking field by exploring the guide to networking roles and opportunities in Germany.
Top 10 Networking Interview Topics Comparison
| Topic | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Explain the OSI Model and its 7 layers | Moderate; conceptual and layered model | Low; mostly theoretical | Clear understanding of network layers and data flow | Learning/troubleshooting network fundamentals | Standardizes networking, modular design, troubleshooting |
| What is the difference between TCP and UDP? | Moderate; protocol concepts at Layer 4 | Medium; requires network knowledge | Insight into transport reliability vs speed trade-offs | Choosing appropriate transport protocols | TCP reliable transfer, UDP low latency and overhead |
| How does DHCP work and what are its components? | Moderate; client-server setup | Medium; DHCP server and network | Automated IP assignment and centralized config | IP management in dynamic networks | Reduces manual errors, efficient IP use, plug-and-play |
| Explain how DNS resolution works | Moderate; multi-step hierarchical process | Low to medium; DNS servers | Fast and reliable domain-to-IP translation | Resolving domain names on the internet | User-friendly addressing, redundancy, caching benefits |
| What is subnetting and how do you calculate subnet masks? | High; requires binary math and planning | Low; mainly administrative | Segmented networks with efficient address use | Network design, IP management | Reduces congestion, improves security, enhances routing |
| Describe the difference between a switch and a router | Low to moderate; device-based knowledge | Medium; requires hardware knowledge | Proper network device deployment and packet forwarding | Designing LANs and WANs | Switch: speed and local forwarding, Router: network routing |
| What are VLANs and how do they work? | Moderate to high; configuration on switches | Medium; VLAN-capable hardware | Logical network segmentation, traffic isolation | Network security and management | Enhanced security, reduced traffic, flexible grouping |
| Explain routing protocols: RIP, OSPF, and BGP | High; protocol-specific configuration | High; powerful routers and resources | Scalable and optimized routing in different networks | Enterprise, ISP, and internet backbone routing | RIP simplicity, OSPF speed, BGP scalability & policy control |
| What is NAT (Network Address Translation) and why is it used? | Moderate; configuration on routers/firewalls | Medium; network devices required | IP address conservation and security layer | IPv4 address management, private to public IP bridging | Conserves IPv4, basic security, reduces address complexity |
| How do you troubleshoot network connectivity issues? | Variable; from simple to complex | Medium to high; tools and access | Efficient problem identification and resolution | Any network-related issue resolution | Structured approach, comprehensive diagnostic tools |
From Theory to Practice: Securing Your Next Networking Role
Navigating the landscape of networking interview questions can feel like traversing a complex digital network itself. From the foundational structure of the OSI model to the practical art of troubleshooting a faulty connection, each question is a node, and your answer is the packet that must reach its destination with precision and clarity. This article has equipped you with a roadmap, offering detailed answers and strategic approaches to the most common challenges you will face.
The key takeaway is this: success in a networking interview is not just about reciting definitions. It's about demonstrating a deep, functional understanding. Employers, particularly in the competitive German market, are not looking for a human textbook; they are searching for a problem-solver who can apply theoretical knowledge to real-world scenarios.
Bridging Knowledge and Application
True mastery is shown when you can articulate the why behind a concept, not just the what. For example, explaining why TCP is chosen over UDP for file transfers (reliability) or why BGP is the backbone of the internet (scalability and policy control) showcases a level of comprehension that sets you apart. The difference between a good candidate and a great one often lies in this ability to connect theory to practical outcomes.
Key Insight: Frame your answers as mini case studies. When explaining NAT, don't just define it. Briefly describe a situation, perhaps from a past project or lab, where NAT was essential for connecting a private network to the internet while conserving public IP addresses. This transforms a dry, academic answer into a compelling demonstration of your skills.
Actionable Steps for Your Final Preparation
As you move forward, focus your efforts on solidifying this practical knowledge. Your final preparation phase should be active, not passive.
- Build and Break: Set up a small virtual lab using tools like GNS3 or Packet Tracer. Configure DHCP, set up VLANs, and establish routing with OSPF. Then, intentionally break things. Can you diagnose why a host isn't getting an IP address or why two subnets cannot communicate? This hands-on practice is invaluable.
- Articulate Your Troubleshooting Process: Go beyond the list of commands. Practise explaining your troubleshooting methodology out loud. Start with the physical layer and work your way up the OSI model, describing what you would check at each step and why. This structured approach is highly valued by hiring managers.
- Research Company-Specific Challenges: Investigate the company you are interviewing with. Are they a large enterprise, a cloud service provider, or an ISP? Their specific environment will dictate the networking challenges they face and, consequently, the focus of their networking interview questions. Tailor your examples to align with their business context.
Mastering these questions is more than an interview tactic; it is a validation of your expertise and a crucial step in your career progression. The concepts we have covered, from subnetting to routing protocols, are the fundamental building blocks of modern digital infrastructure. Your ability to command them confidently opens doors to impactful roles where you will design, build, and maintain the networks that power our connected world. For a deeper dive into practical application and career advancement in network security, you might find valuable insights into strategies for securing network roles.
Ultimately, your goal is to walk into that interview room not just prepared, but confident. This confidence comes from knowing you haven't just memorised facts but have genuinely internalised the principles of networking. With dedicated practice and a focus on real-world application, you are well on your way to securing your next great role.
Ready to put your knowledge to the test and get expert feedback before your big interview? iknowly connects you with verified professionals from top German companies for 1:1 mock interviews and personalised coaching. Refine your answers and gain insider insights to confidently answer any networking interview questions an employer throws your way. Book your session on iknowly today and take the final step toward your dream job.

